What is it?:
The Heartbleed Bug is a vulnerability in the OpenSSL software library. A missing bounds check in the handling of the TLS heartbeat extension can be used to reveal up to 64k of memory to a connected client or server. This weakness causes multiple information disclosure vulnerabilities, which give attackers access to sensitive information to aid in further attacks. After taking advantage of this vulnerability, attackers can eavesdrop on communications, steal data directly from the services and users, and gives them the ability to impersonate services and users.
Identification:
When trying to identify this vulnerability, there are multiple tools and some manual ways to identify it. For our lesson, we will be covering two tools for automated identification, which is Nmap and Metasploit. Both of these are available on Kali Linux and require no additional setup to identify the Heartbleed Bug. The first tool we will cover for identification is Nmap.
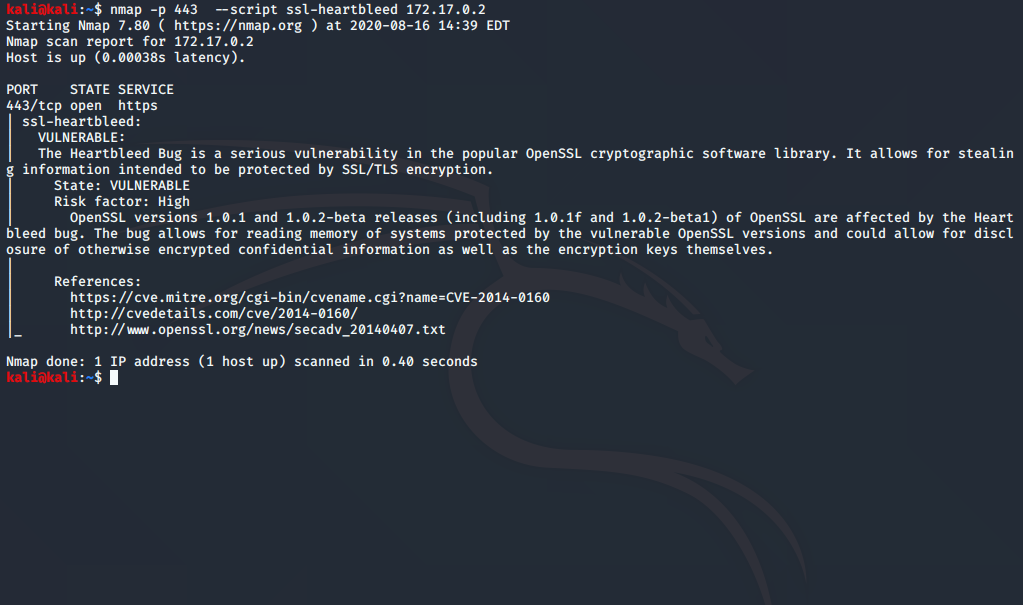
To identify this vulnerability using Nmap, we need to utilize the ssl-heartbleed script. The command for running this script would look like "nmap -p 443 --script ssl-heartbleed <target>". Replace the <target> field with the IP or URL of your desired target. For example, "nmap -p 443 --script ssl-heartbleed 172.17.0.2" would be a correct way of running the script.
Let's break down this command and explain what each of these fields does. The -p option tells Nmap which port to scan when launched. In our case, we are telling Nmap to scan port 443 when launched. The --script field designates a script to be used by the Nmap scripting engine (NSE). For this field, we told Nmap's scripting engine to run the ssl-heartbleed script.
1.1
Image 1.1 is an example of the command running against a vulnerable target. We can see that Nmap has returned a few informative fields after its scan. The "VULNERABLE" field explains the vulnerability and why it matters. The "STATE" field gives the user running the script a status about the vulnerability. From the scan we performed our "STATE" field informs us our target is vulnerable to the Heartbleed Bug. The final piece of information users should pay attention to is the "Risk factor" field. The "Risk factor" field informs a user about the level of risk the vulnerability presents and a description of the potential impact.
The next tool we will use for identifying this vulnerability is an auxiliary scanner module located in Metasploit. To use the scanner module, we first need to know the path for it so we can select it as the active tool. Finding this information can be done by running the search command with the term heartbleed. Image 1.2 shows an example of the search command being run and its results. Metasploit has informed us there are two options we can use, for our lesson we will be using the auxiliary/scanner/ssl/open_ssl module.
1.2
After we have identified which module we want to use, we need to set our module as active, and we need to set any additional options. To make our module active, we use the command "use auxiliary/scanner/ssl/openssl_heartbleed", which will tell Metasploit this is the module we wish to use. As you can see in image 1.2, after using this command, our console now displays "auxiliary(scanner/ssl/openssl_heartbleed)" in the CMD line to inform us the module is active.
To figure out what options need to be set for this module, run the "show options" command. Running the "show options" command for this module gives us a good bit of options. For the purpose of the identification step in this lesson, we only need to worry about the "RHOSTS" option. We will need to set the "RHOSTS" option with our target information. To do this, run the command "set rhosts Target" and replace the word Target with your target's IP or URL information. Once this is complete, you can run your module by typing the command "run" in the console and pressing enter. See image 1.3 for an example of setting the "RHOSTS" option and running the module.
1.3
After running the module, we are informed our target is vulnerable. Image 1.3 shows the response "Heartbeat response with leak" indicating our target is susceptible to the Heartbleed Bug. Now that you have identified the vulnerability using two different methods, we will discuss how to exploit it..
Exploitation:
If you were to use the command "info auxiliary/scanner/ssl/openssl_heartbleed" we are informed there are three different actions our module can perform. These actions are "SCAN" which we used in the identification phase to find the vulnerability, "DUMP" which will dump contents of the vulnerable system's memory, and "KEYS" which is used to extract private keys from memory.
1.4
We can set the action we want to use by typing "set action <actionName>" For example, you will want to use the command "set action DUMP" to set the DUMP action. See image 1.5 for an example of the "set action" command being run, and the output of the "show options" command after "DUMP" has been set as the action.
1.5
After everything has been set you can now execute the exploit by entering the "run" command. As you can see in image 1.6 the module has run gotten a response from the vulnerable server, and the results have been output to a bin file.
1.6
When taking advantage of the Heartbleed Bug an attacker needs to run this module more than once to gain valuable information. The need to run the module more than once is due to it dumping memory from that moment. At any given time, its memory could contain valuable information or data that an attacker doesn't need. For example, in image 1.7 the dump we performed informed us someone was trying to access a webpage that didn't exist on the vulnerable server. If someone had entered credentials before our dump, we would have had the ability to harvest them from memory.
1.7
Now that you know the basics of identifying and exploiting this vulnerability get out there and hack the planet!
Mitigation:
Affected users should upgrade to OpenSSL 1.0.1g. Users unable to immediately upgrade can alternatively recompile OpenSSL with -DOPENSSL_NO_HEARTBEATS.